
Next
Security:
Control and visibility
Dropbox is designed with multiple layers of protection, including secure data transfer, encryption, network configuration, and application-level controls distributed across a scalable, secure infrastructure.
Dropbox users can access files and folders at any time from a number of interfaces, including the desktop, web, and mobile clients, or through third-party applications connected to Dropbox. Each has security settings and features that process and protect user data while ensuring ease of access. All of these clients connect to secure servers to provide access to files, allow file sharing with others, and update linked devices when files are added, changed, or deleted.
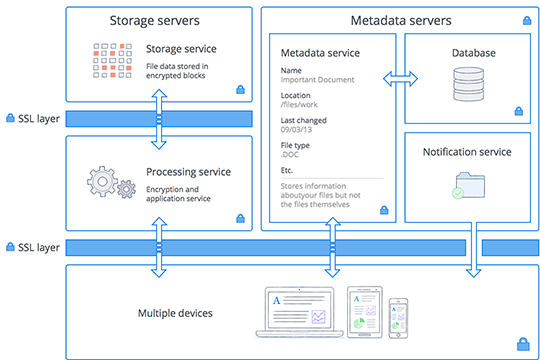
This service handles all processing for the Dropbox applications. Each file is split into blocks, and each block is hashed and encrypted using a strong cipher. Only blocks that have been modified are synced. When a change is made, new or modified blocks are processed and transferred to the storage service.
The actual contents of users' files are stored in encrypted blocks with this service. Each individual encrypted file block is retrieved based on its hash value, and an additional layer of encryption is provided for all file blocks at rest using a strong cipher.
Basic information about user data (including file names and types), called metadata, is kept in its own discrete storage service separate from file blocks. This metadata acts as an index for data in users' accounts, and is sharded and replicated as needed to meet performance and high availability requirements.
This is a separate service dedicated to monitoring if changes have been made to Dropbox accounts. No file data or metadata is stored or transferred here. Instead, clients establish a long poll connection to this service and wait for a change, which then signals a change to the relevant clients
Both dedicated internal security teams and third-party security specialists protect these services through the identification and mitigation of risks and vulnerabilities. These groups conduct regular application, network, and other security testing and auditing to ensure the security of our back-end network. In addition, our responsible disclosure policy promotes the discovery and reporting of security vulnerabilities.
Dropbox corporate and production systems are housed at third-party subservice organization data centers and managed service providers located in the United States. These third-party service providers are responsible for the physical, environmental, and operational security controls at the boundaries of Dropbox infrastructure. Dropbox is responsible for the logical, network, and application security of our infrastructure housed at third-party data centers.
Dropbox file data at rest is encrypted using 256-bit Advanced Encryption Standard (AES). To protect data in transit between Dropbox apps (currently desktop, mobile, API, or web) and our servers, Dropbox uses Secure Sockets Layer (SSL)/Transport Layer Security (TLS) for data transfer, creating a secure tunnel protected by 128-bit or higher Advanced Encryption Standard (AES) encryption.
Dropbox does certificate pinning on our desktop and mobile clients. Certificate pinning is an extra check to make sure that the service you're connecting to is really who they say they are, and not an imposter. We use it to guard against other ways that skilled hackers may try to spy on your activity.
For end points we control (desktop and mobile) and modern browsers, we use strong ciphers and support perfect forward secrecy. By implementing perfect forward secrecy, we've made it so our private SSL key can't be used to decrypt past Internet traffic. This adds extra protection to encrypted communications with Dropbox, essentially disconnecting each session from all previous sessions. Additionally, on the web we flag all authentication cookies as secure and enable HTTP Strict Transport Security (HSTS).
Dropbox's key management infrastructure is designed with operational, technical, and procedural security controls with very limited direct access to keys. Encryption key generation, exchange, and storage is distributed for decentralized processing.
Dropbox manages file encryption on users' behalf to remove complexity, support advanced product features and enable strong cryptographic control. File encryption is protected by production system infrastructure security controls and security policies. Access to production systems is restricted with unique SSH key pairs, and security policies and procedures require protection of SSH keys. An internal system manages the secure public key exchange process, and private keys are stored securely.
Find more details about our security architecture in our Dropbox for Business security whitepaper.